When deploying new Windows devices, Windows Autopilot leverages the OEM-optimized version of Windows 10 that is preinstalled on the device, saving organizations the effort of having to maintain custom images and drivers for every model of device being used.
Instead of re-imaging the device, your existing Windows 10 installation can be converted into a “ready” state, applying settings and policies and installing apps.
After deployment, Windows 10 devices can be managed by Microsoft Intune.
This is a perfect tool for small and medium-sized business which do not have SCCM or MDT to automate the deployment of computers in their organization.
Windows Autopilot and InTune enables you to:
- Automatically join devices to Azure Active Directory (Azure AD) and Active Directory (via Hybrid Azure AD Join) at the same time.
- Auto-enroll devices into Microsoft Intune.
- Install all company applications from Intune Portal.
- Silently encrypt the local drive with BitLocker and store recovery key in Azure AD.
- Enroll Device in Windows Update for Business and keep all Windows 10 workstation updated.
- Apply some of Groups Settings from Intune instead from Local AD
Software and OS requirements
- Windows 10 v1809 or greater.
- The following editions are supported:
- Windows 10 Pro
- Windows 10 Pro Education
- Windows 10 Pro for Workstations
- Windows 10 Enterprise
- Windows 10 Education
- Windows 10 Enterprise 2019 LTSC
Licensing requirements
One of the following is required:
- Microsoft 365 Business subscriptions
- Microsoft 365 F1 subscriptions
- Microsoft 365 Academic A1, A3, or A5 subscriptions
- Microsoft 365 Enterprise E3 or E5 subscriptions, which include all Windows 10, Office 365, and EM+S features (Azure AD and Intune).
- Enterprise Mobility + Security E3 or E5 subscriptions, which include all needed Azure AD and Intune features.
- Intune for Education subscriptions, which include all needed Azure AD and Intune features.
- Azure Active Directory Premium P1 or P2 and Microsoft Intune subscriptions (or an alternative MDM service).
Local AD Requirement
AD Connect (the most recent version)
Windows Server 2016 to install Intune Connector
An overview of deployment steps
- Create new OU and new GPO to configure SCP entry in the registry of your devices.
- Configure Delegation to new OU for computer object which is going to have Azure Intune Connector
- Reconfigure AD Connect to include new OU in syncing scope
- Install Intune Connector on windows 201q6 server hosted on-premises.
- Configure a couple Groups in Azure AD
- Configure Device Settings to allow users to join devices to Azure AD
- Configure automatic MDM enrollment
- Create and assign an Autopilot deployment profile
- Create and assign a Domain Join profile
- Load Hardware Hashes from workstation to Azure AD
- Boot up workstation to start deployment.
Let’s review the steps that this goes through:
- The workstation boots up and connects to the network.
- Autopilot profile is downloaded to workstation.
- Workstation is asking for Azure AD credentials , which are used to enroll the device in Intune. The workstation does not join Azure AD.
- The device enrolls in Intune, using the “Domain Join” device configuration profile settings, the device will request an Offline Domain Join blob from Intune. Intune passes this request to the Offline Domain Join connector service and gets back the blob. That blob is passed back to the client PC.
The client PC applies the Offline Join Blob blob and then restarts to complete the Active Directory join process. - The workstation won’t reboot if it can’t find a domain controller.The most common errros on this steps is “Something went wrong” with error 0x80070774.
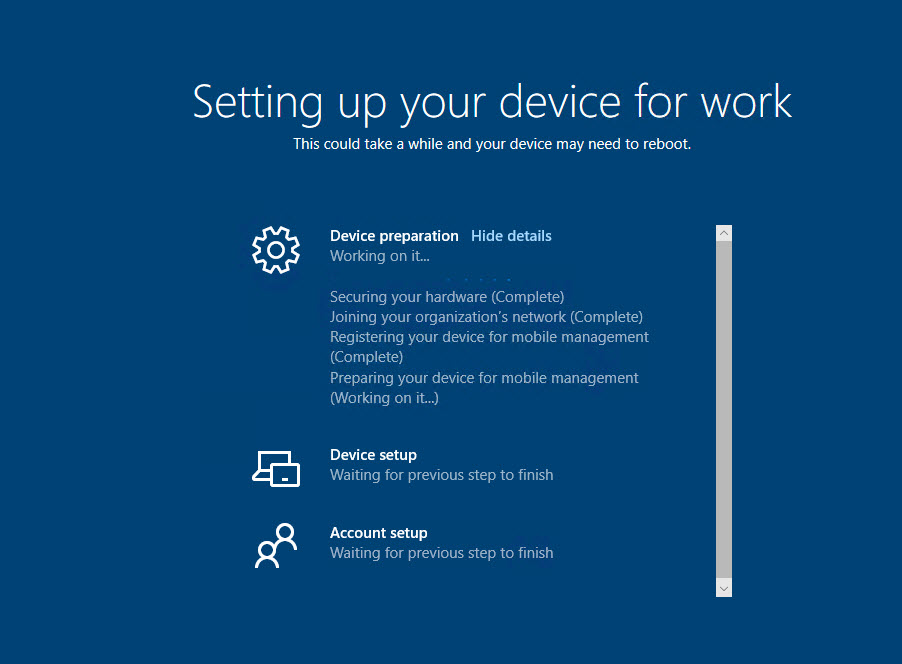
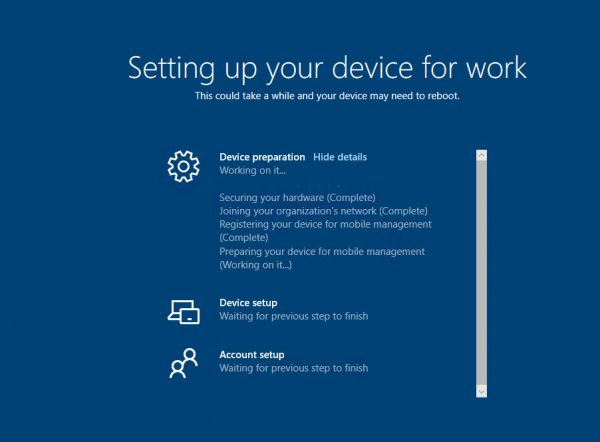
- After the reboot, the enrollment status page (ESP) will be shown to process the device configuration .
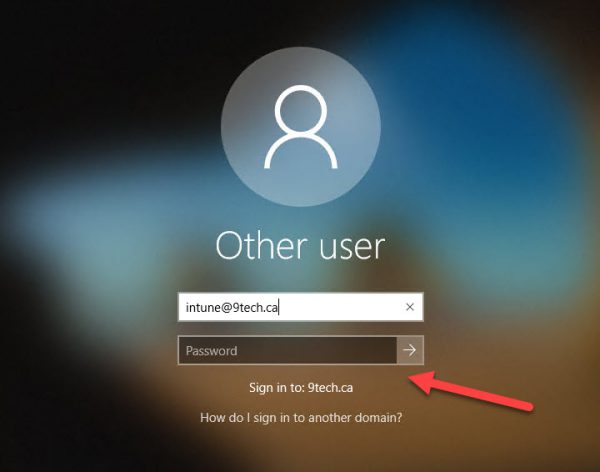
- Now, the user will be asked to sign in again , but this time using their Active Directory credentials.
The AD account signs on, goes through the first sign-on experience and then desktop is presented.
Create new OU and new GPO to configure SCP entry in the registry of your devices.
Create new OU where provisioned Computers will be created.
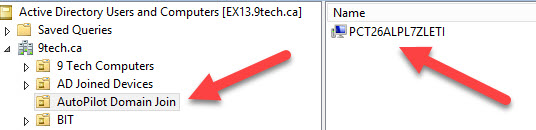
In our case, we created the following OU
OU=AutoPilot Domain Join,DC=9tech,DC=ca
For a computer to be able joined in Azure AD, we will need to configure SCP entry settings using the following GPO
Create a Computer-based GPO with the following names and settings.
| OU | Policy Name |
| OU=AutoPilot Domain Join,DC=9tech,DC=ca | Hybrid Azure AD join |
Configure client-side registry setting for SCP
Use the following example to create a Group Policy Object (GPO) to deploy a registry setting
Create new GPO (Hybrid Azure AD join) and locate the following path: Computer Configuration > Preferences > Windows Settings > Registry
Right-click on the Registry and select New > Registry Item
-
- On the General tab, configure the following
- Action: Update
- Hive: HKEY_LOCAL_MACHINE
- Key Path: SOFTWARE\Microsoft\Windows\CurrentVersion\CDJ\AAD
- Value name: TenantId
- Value type: REG_SZ
- Value data: The GUID or Directory ID of your Azure AD instance (This value can be found in the Azure portal > Azure Active Directory > Properties > Directory ID)
Click OK
- Right-click on the Registry and select New > Registry Item
- On the General tab, configure the following
- .Action: Update
- Hive: HKEY_LOCAL_MACHINE
- Key Path: SOFTWARE\Microsoft\Windows\CurrentVersion\CDJ\AAD
- Value name: TenantName
- Value type: REG_SZ
- Value data: Your verified domain name if you are using federated environment such as AD FS. Your verified domain name or your onmicrosoft.com domain name, for example, contoso.onmicrosoft.com if you are using managed environment
Click OK
- Close the editor for the newly created GPO
- Link the newly created GPO (Hybrid Azure AD join) to the desired OU (OU=AutoPilot Domain Join,DC=9tech,DC=ca) containing domain-joined computers that belong to your controlled rollout population
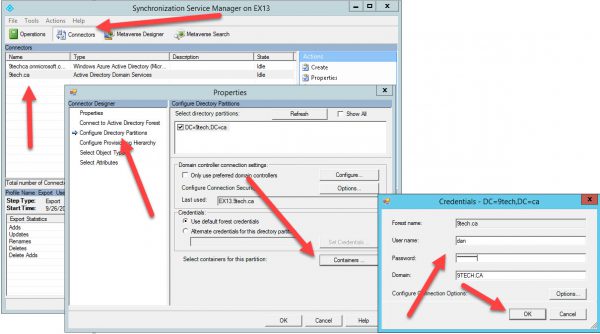
Login to AD Connect Server and run Synchronization Service Manager
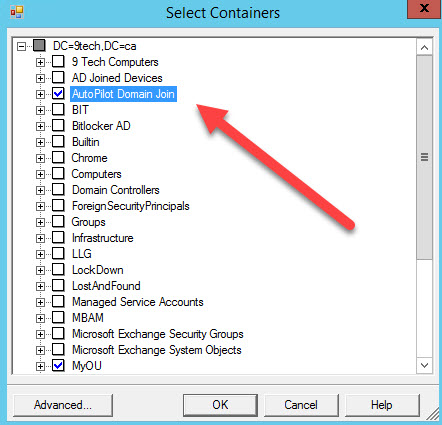
Navigate to containers using the following figure
Select your OU, Save, and Exit
Open Powershell on AD Connect Server and run the following Powershell Command.
Start-ADSyncSyncCycle -PolicyType initial
We need to run this command each time we make modification in OU Scope
You can run this script on AD Connect server during deployment to speed up domain join operation to Azure AD.
Script will run sync process every 300 sec.
$i=1
for(;$i -le 10;$i++)
{
Start-ADSyncSyncCycle -PolicyType delta
Write-Host $i
start-sleep -seconds 300
}
Configure Delegation to new OU for computer object which is going to have Azure Intune Connector
The Intune Connector for your Active Directory creates autopilot-enrolled computers in the on-premises Active Directory domain.
The computer that hosts the Intune Connector must have the rights to create the computer objects within the domain.
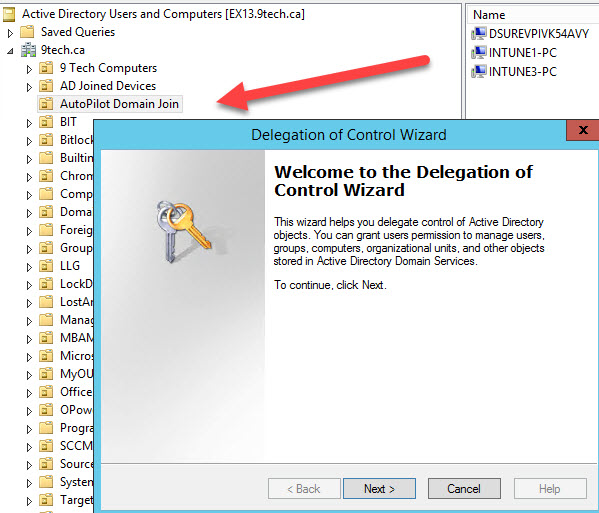
Open Active Directory Users and Computers (DSA.msc).
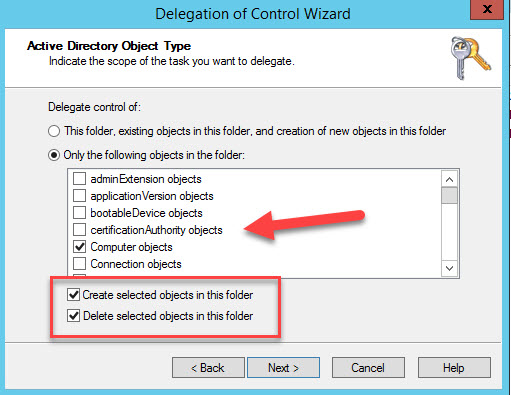
Right-click the organizational unit that you’ll use to create hybrid Azure AD-joined computers, and then select Delegate Control.
In the Delegation of Control wizard, select Next > Add > Object Types.In the Object Types pane, select the Computers check box, and then select OK.
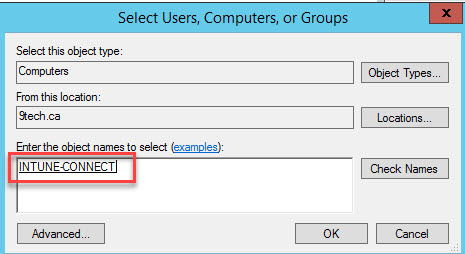
In the Select Users, Computers, or Groups pane, in the Enter the object names to select box, enter the name of the computer where the Connector is installed.
Select Create a custom task to delegate >
Next. Select the Only the following objects in the folder checkbox, and then select the Computer objects, Create selected objects in this folder, and Delete selected objects in this folder checkboxes.
Under Permissions, select the Full Control checkbox.
This action selects all the other options.
Select Next, and then select Finish.
Install the Intune Connector
The Intune Connector for Active Directory must be installed on a computer that’s running Windows Server 2016 or later. The computer must also have access to the internet and your Active Directory.
- In Intune, select Device enrollment > Windows enrollment > Intune Connector for Active Directory (Preview) > Add connector.
- Follow the instructions to download the Connector.
- Open the downloaded Connector setup file, ODJConnectorBootstrapper.exe, to install the Connector.
- At the end of the setup, select Configure.
- Select Sign In
- Enter the user Global Administrator or Intune Administrator role credentials.
- The user account must have an assigned Intune license.
- Go to Device enrollment > Windows enrollment > Intune Connector for Active Directory (Preview), and then confirm that the connection status is Active.
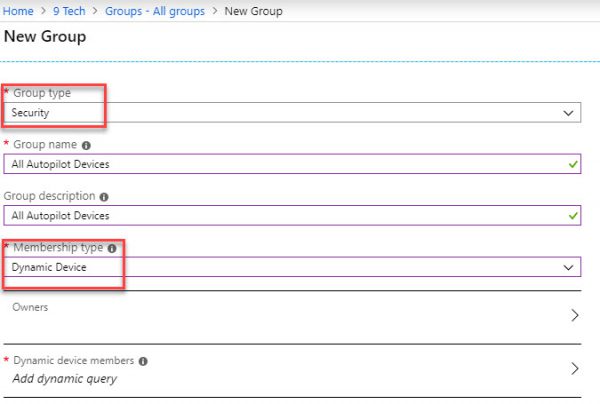
Create Azure AD Group for AutoPilot Devices
Navigate to Home>9 Tech>Groups – All groups
Group Name=All Autopilot Devices
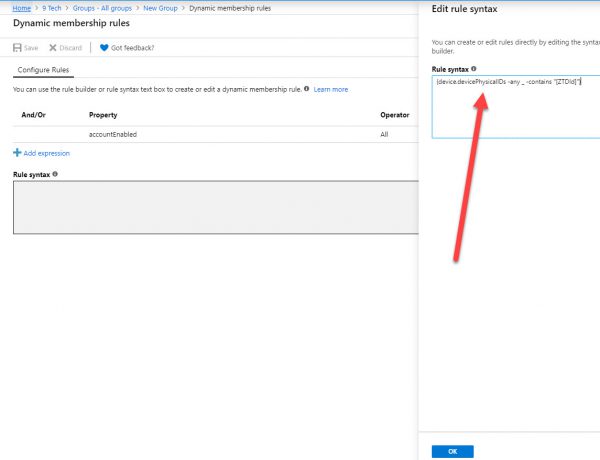
MemberShip Type = Dynamic
(device.devicePhysicalIDs -any _ -contains “[ZTDId]”)
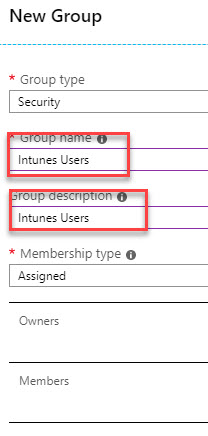
Create Intune Users Group
To limit who can join devices in Intune, create the following group
Group Name=Intune Users
Membership type = Assigned
Members = Add all users which will be using Intune and AutoPilot
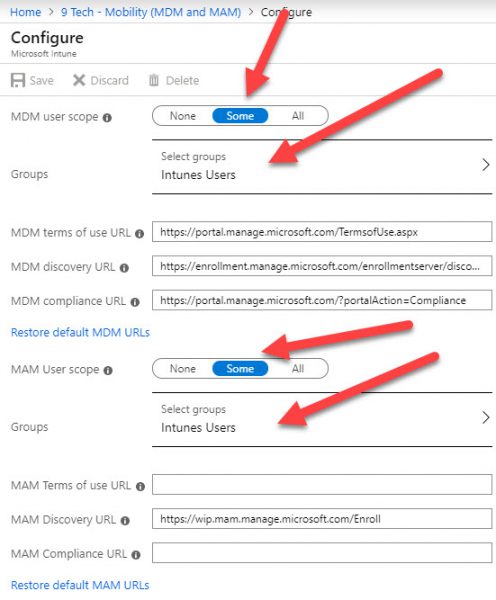
Configure MDM Global Settings
Navigate to
Home\9 Tech – Mobility (MDM and MAM)\Configure
MDM User scope = Some= ADD Intune Users (Group created in the previous step )
MDM User scope = Some = ADD Intune Users (Group created in the previous step )
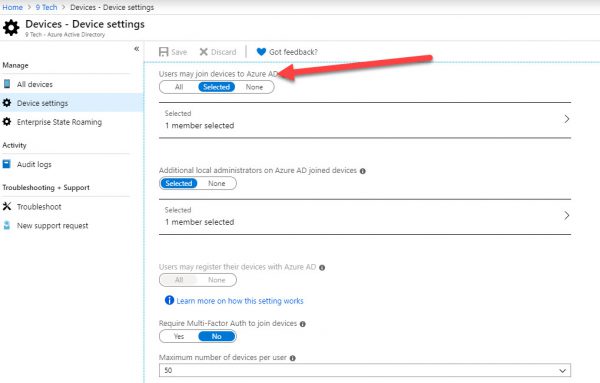
Configure Device Settings
This setting will allow only members of Intune Users groups to join a workstation to Azure AD
Navigate to
Home\Azure Active Directory\Devices\Device setting
Select the users and groups that are allowed to join devices to Azure AD= Selected = Intune Users
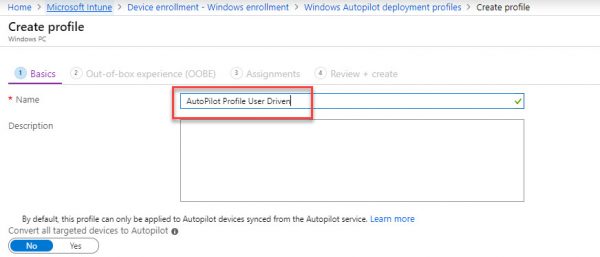
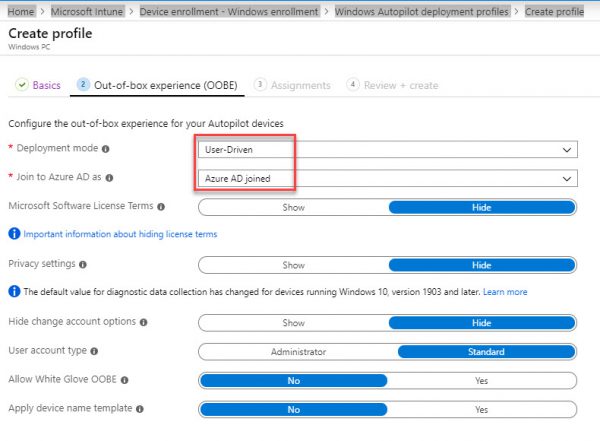
Create and assign an Autopilot deployment profile
-
In Intune, select Device enrollment > Windows enrollment > Deployment Profiles > Create Profile.
-
Type a Name= AutoPilot Profile User Driven
- For Deployment mode, select User-driven.
- In the Join to Azure AD as box, select Hybrid Azure AD joined (Preview).
- Do not select Out-of-box experience (OOBE) and then select Save.
-
Select Create to create the profile.
-
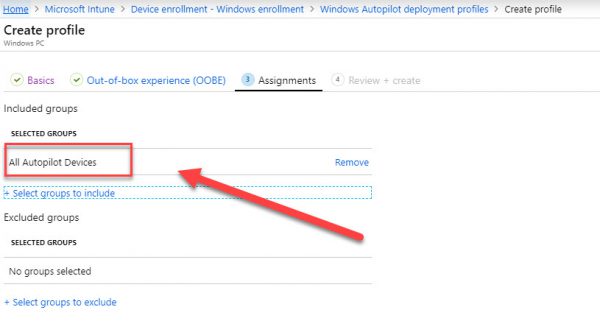
In the profile pane, select Assignments.
-
Select Select groups.
-
In the Select groups pane, select the AutoPilot All Autopilot Devices device group, and then click Select.
It takes about 15 minutes for the device profile status to change from Not assigned to Assigning and, finally, to Assigned.
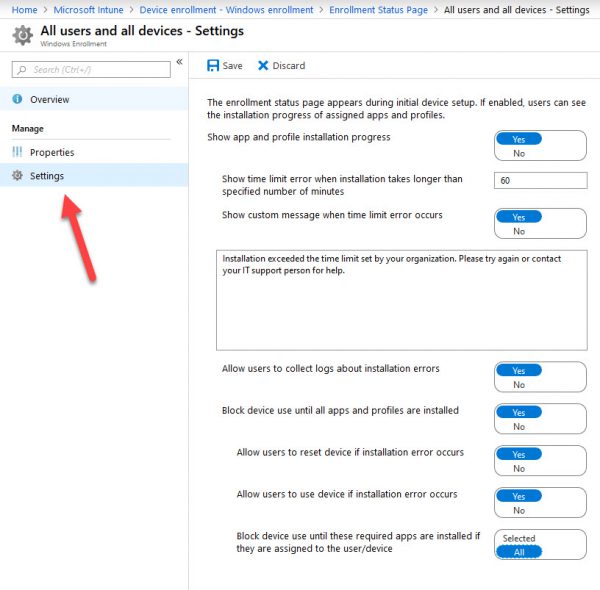
Turn on the enrollment status page
-
In Intune, select Device enrollment > Windows enrollment > Enrollment Status Page.
-
In the Enrollment Status Page pane, select Default > Settings.
-
In the Show app and profile installation progress box, select Yes.
-
Configure the other options as needed.
-
Select Save.
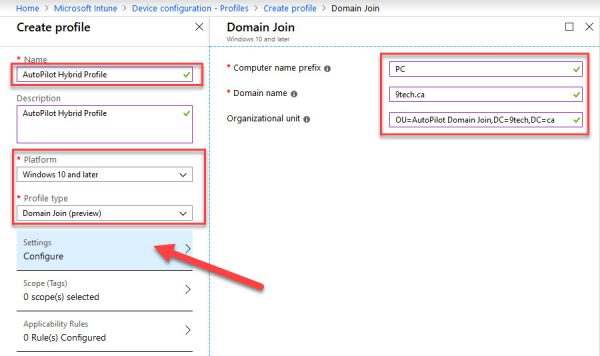
Create and assign a Domain Join profile
- In Intune, select Device configuration > Profiles > Create Profile.
- Enter the following properties:
- Name: AutoPilot Hybrid Profile
- Description: Enter a description for the profile.
- Platform: Select Windows 10 and later.
- Profile type: Select Domain Join (Preview).
- Select Settings, and then provide a
Computer name prefix = PC
Domain name = 9tech.ca
Organizational unit in DN format OU=AutoPilot Domain Join,DC=9tech,DC=ca
Do not experiment with computer prefix putting %serial% variable. It will fail on Offline Domain Join Process.
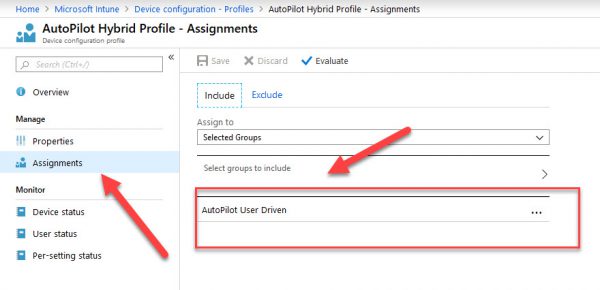
Select OK > Create
The profile is created and displayed in the list.
To assign the profile. navigate to Assignments and select AutoPilot User Driven Group.
Turn on default enrollment status page for all users
-
In Intune choose Device enrollment > Windows enrollment > Enrollment Status Page.
-
In the Enrollment Status Page blade, choose Default > Settings.
-
For Show app and profile installation progress, choose Yes.
-
Choose the other settings that you want to turn on and then choose Save.
Registering Devices
Register devices from an OEM
Yes, you will need to install Windows 10 to an old device to get the hardware key.
Extract Hardware Hashes from existing devices
I created the following three files which will automate all the processes.
Put all these three files on a USB drive.
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\WindowsStore] “AutoDownload”=dword:00000002
———————————————————————————————-
@echo off color 06 ECHO -------------------------------------------------------------------------- ECHO Collecting Hardware Key Powershell.exe -ExecutionPolicy Bypass -File "%~dp0\Get-WindowsAutoPilotInfo.ps1" -OutputFile %~dp0\%computername%.csv ECHO ----------------------------------------------------------------------------- Echo Hardware Keys has been uploaded to USB DRIVE reg import "%~dp0\disableST.reg" ECHO -------------------------------------------------------------------------- ECHO Microsoft Store updates have been disabled. powershell -executionpolicy Bypass -Command "Get-AppxPackage -AllUsers | Remove-AppxPackage" ECHO ------------------------------------------------------------------------------- ECHO All Microsoft Store Applications have been removed. ECHO ------------------------------------------------------------------------------- ECHO Press any key to sysprep computer and shutdown. ECHO --------------------------------------------------------------------------- pause Echo --------------------------------------------------------------------------- ECHO Executing SYSPREP...System will go down shortly. DO ECHO DO NOT SHUTDOWN SYSTEM C:\Windows\System32\Sysprep\Sysprep.exe /generalize /oobe /shutdown /quiet TIMEOUT 5
Get-WindowsAutoPilotInfo.ps1
Download Get-WindowsAutoPilotInfo.ps1 from the following location
https://www.powershellgallery.com/packages/Get-WindowsAutoPilotInfo/1.6
Run a file to export key
Right-click and run file as Administrator
- Get-WindowsAutoPilotInfo.ps1 will export hardware ID to a USB drive
- Microsoft Store updates will be disabled
- All Microsoft apps will be removed from PC
- Sysprep will be run and the system will be shut down.
Deploying Workstation
Boot up workstation.
Pick up region
Pick up Keyboard
Skip keyboard layout
On next screen, you will get customized message welcoming you to your domain
This is a sign that workstation got Auto Pilot Profile from Azure.
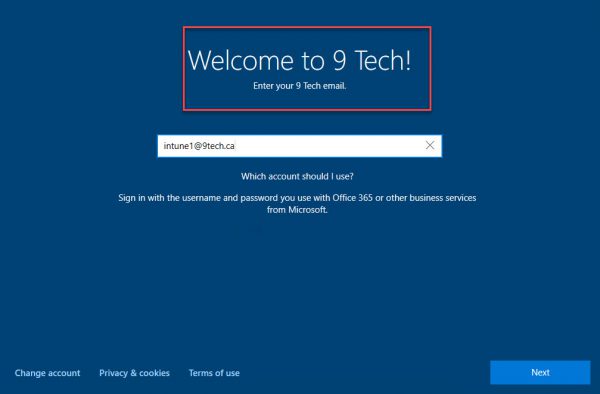
Type your Office 365 ID.
After you authenticate, you will receive Enrollment page with status of enrollment.
As you can see , workstation has been joined to local AD Domain.
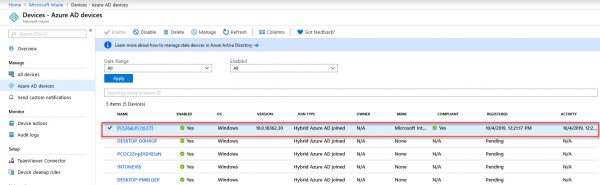
- The Autopilot Devices pane in the Intune in the Azure portal. Select Device enrollment > Windows enrollment > Devices.
- The Azure AD devices pane in the Intune in the Azure portal. Select Devices > Azure AD Devices.
- The Azure AD All Devices pane in Azure Active Directory in the Azure portal by selecting Devices > All Devices.
- The Autopilot Devices pane in the Intune in the Azure portal. Select Device enrollment > Windows enrollment > Devices.
- The Azure AD devices pane in the Intune in the Azure portal. Select Devices > Azure AD Devices.
- The Azure AD All Devices pane in Azure Active Directory in the Azure portal. Select Devices > All Devices.
- The All Devices pane in the Intune in the Azure portal. Select Devices > All Devices.
4 Oct 2019

Hi Dan,
I love your article. Thanks for sharing. I’m trying to run your batch file to generate hardware hash and OOBE at the same time but i got this error sysprep was not able to validate your windows installation. We’re using volume licensing in the school. Is that going to be a problem?
Appreciate your reply. Thanks.
Sysprep must run successfully. You will need to see what is exact error when you run sysprep.
Hey Dan,
thank you very much!
Your tutorial is the best from all tutorials i found in the web!
I have 2 problems…
1. “My device appears under Azure AD Devices with the Join Type Azure AD Joined not Hybrid Azure AD Joined.” is that normal? If not what do I have to do so that it is correct?
2. “After installation, the domain is shown to me and I can log in with a domain account, then my device is configured and that’s it. Nothing happens here and I’m stuck in the point, only after I have logged the user out and logged in does it work, that’s not normal or?” What am I doing wrong?
Thank you!
The device should be joint in Azure AD and in Local Domain at the same time. You will be able to login to workstation using the local admin account. If you configure any application in Intune, the application will be installed after you login.
Hello Dan
Thanks for sharing this interesting workaround with us. I think I followed every step of your instructions. I am using specops os deploy for the schoolpc’s. Some of them have to logon local other pc’s have to log on in the cloud that’s why I followed your instructions.
So I deployed the OS (Windows 10 1909) automatically put the pc in the OU_”Autopilot Domain Join” .
Verified the Azure AD where it says “jointype: Hybrid Azuer AD joined” and registered ” in progress” .
Finally I ran “Export Key and Sysprep to USB.bat”
All goes well untill I have to restart the pc than I get a blue screen with the following message:
Recovery
Your PC/device needs to be repaired
The BCD file doesn’t contain valid info and so on…
File:/BCD
Error code : 0x0000098
….
What could be the issue here ?
Kind regards
I had the same issue on one workstation. I wasn’t able to figure out what happened. This has nothing to do with Intune. It is Sysprep issue.
Just install windows on top of that, and on the end of installation will continue the process automatically.
You can run this step next time instead of Sysprep.
How to Factory Reset Windows 10
/Dan