OVERVIEW
This article shows you how to create and configure a Windows VM and log in with Azure AD-based authentication using RDP.
Default Microsoft configuration needs some additional steps, which are not listed on the Microsoft site.
We can increase the security of Windows virtual machines in Azure by integrating with Azure
AD authentication.
We can now use the Azure AD authentication platform to RDP into a Windows Server 2019 Datacenter edition or Windows 10 1809 and later.
ENABLE AZURE AD AUTHENTICATION ON NEW VM
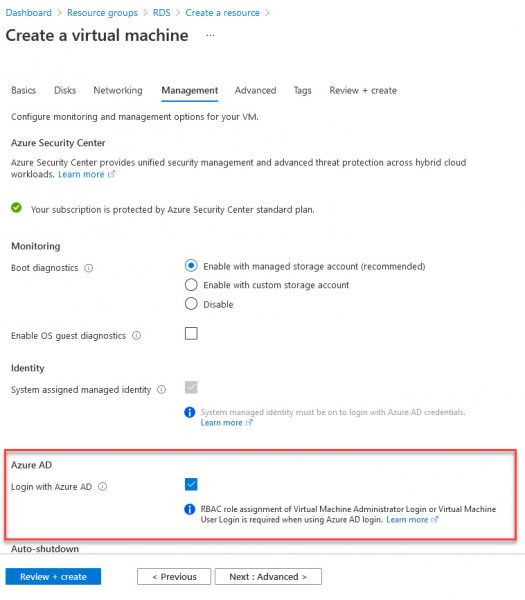
During VM creation navigate to the management tab and enable the option to log in with AAD credentials under
the Azure Active Directory section from Off to On as the figure shows.
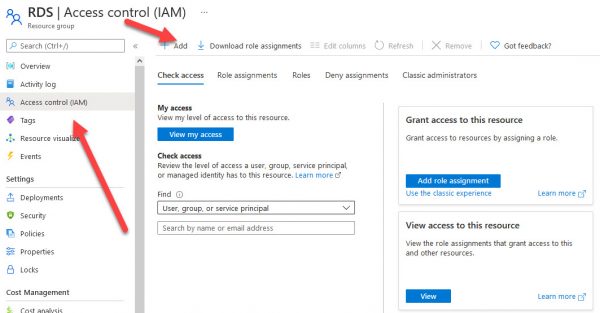
ADD AZURE PERMISSION TO LOG ON TO THE VM
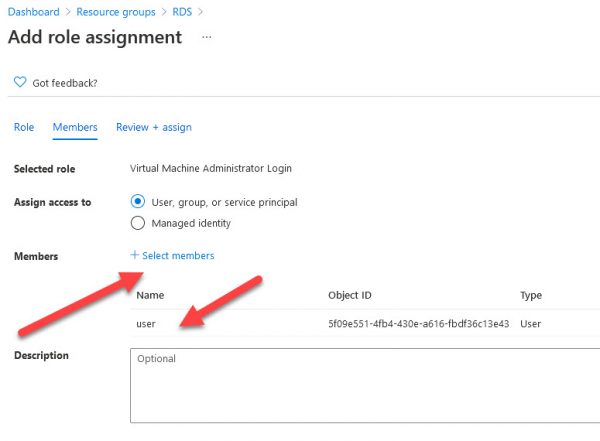
Navigate to your Resource group and add a role assignment.
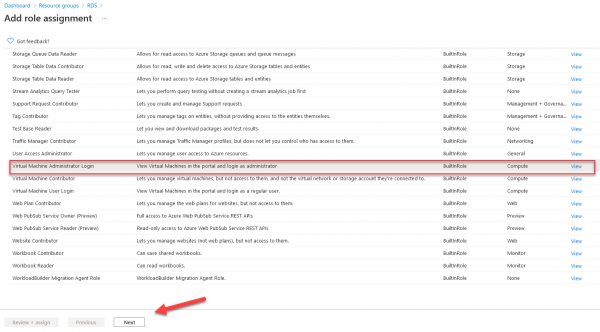
Select Virtual Machine Administrator Login or Virtual Machine User Login
Add your account or group you will be using to authenticate.
CHANGE USER AUTHENTICATION AND SECURITY LAYER ON VM
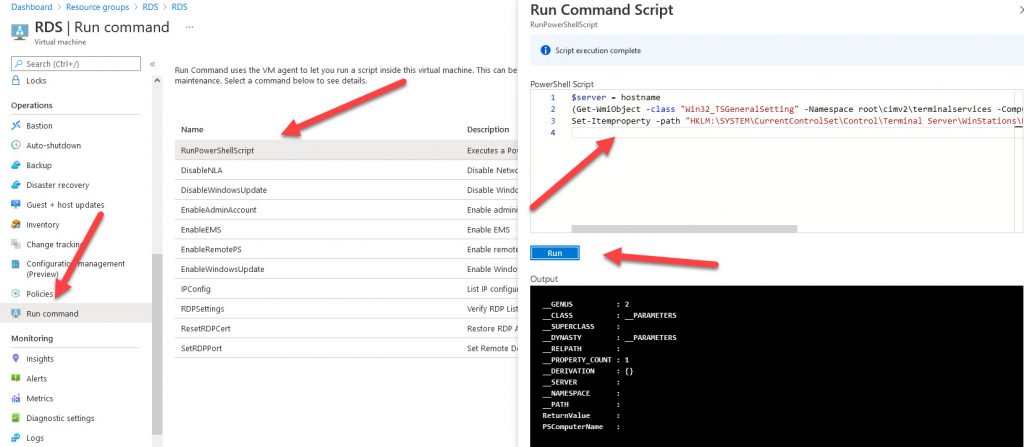
Navigate to your VM to Run command / RunPowerShellScript paste the following commands and run.
These commands will disable the requirement that users must be authenticated at connection time.
$server = hostname (Get-WmiObject -class "Win32_TSGeneralSetting" -Namespace root\cimv2\terminalservices -ComputerName $server -Filter "TerminalName='RDP-tcp'"). (0) Set-Itemproperty -path "HKLM:\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp" -Name 'SecurityLayer' -value 0
CREATE CUSTOM RDP FILE
Open notepad and paste the following content to file.
Change IP address and username. Save file with .rdp extension
full address:s:200.200.200.200:3389 prompt for credentials:i:0 authentication level:i:2 enablecredsspsupport:i:0 username:s:.\AzureAD\user@dand.onmicrosoft.com domain:s:AzureAD
LOGIN TO VM
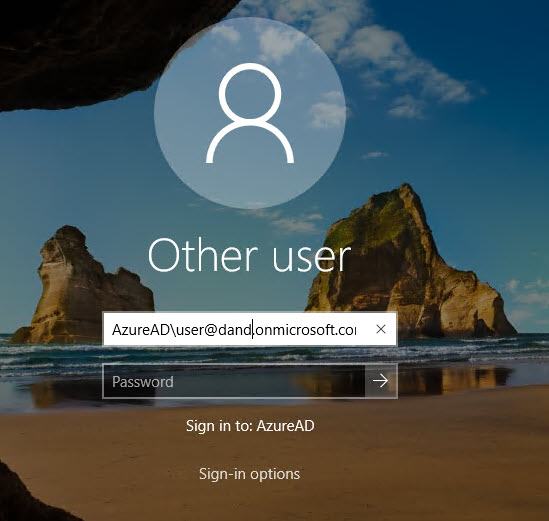
Doube clicks on the RDP file and login to your VM. A screen will look like this. Be sure “AzureAD\” is in the front of the user name (UPN Name)
AN ISSUE WITH MFA-ENABLED ACCOUNTS.
This configuration is not going to work if you have MFA enabled on the account you are using to log in. You will get the following error if you try to log in with MFA enabled account
“The sign-in method you’re trying to use isn’t allowed. Try a different sign-in method or contact your system administrator.”
You can configure the Azure Conditional Access policy using the following article