This article shows how to create Azure Policy Assignments to prevent Azure Administrators or Devepores from creating expensive Virtual Machines. and create some resources types (for example express Route)
We will cover steps using Azure Portal and PowerShell
We will be using the following existing two policies
• Allowed virtual machine size SKUs Policy Assignment
• Not allowed resource types
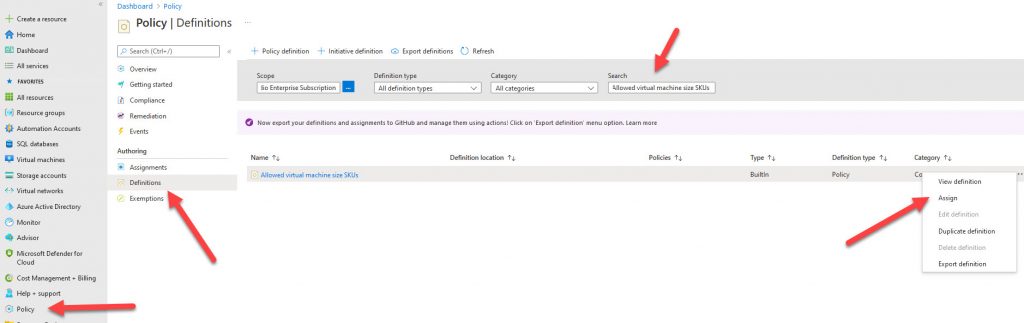
Navigate to Policy-Definitions, search for Allowed virtual machine size SKUs definitions. Select Assign form right menu
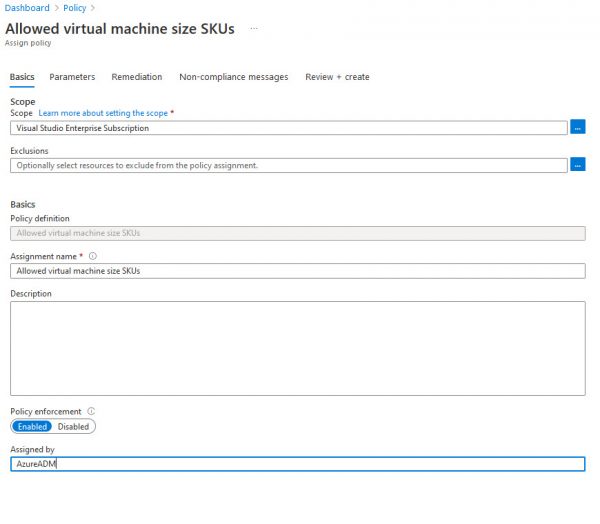
On the Basic tab leave it as default. By default, this policy will be assigned to the whole subscription
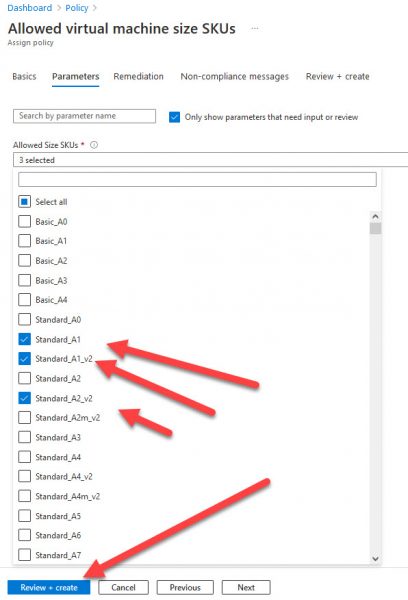
Navigate to the Parameters tab and select all SKUs which you want to be available for your users
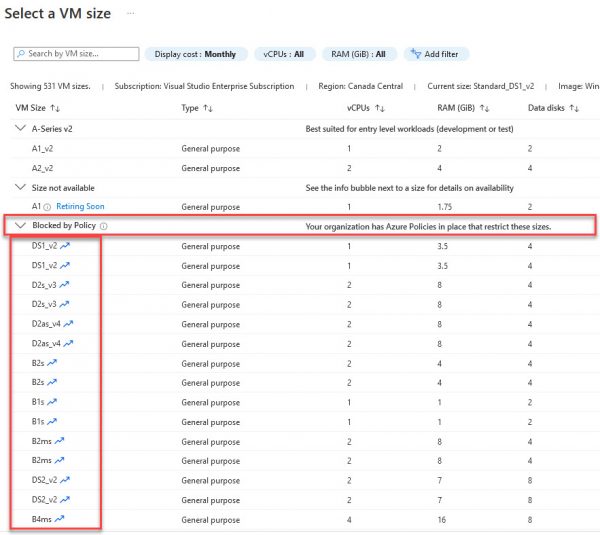
After you assign a policy, this is a screen which will be available during VM creation. The end-users will see which VM is blocked and which are allowed.
Setup Policy Assignment using PowerShell
You can use this script to create policy assignment. Just add your SKUs in $SKUs variable.
$Subscriptionid=”XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX”
$location=”Canada Central”
# Create a Azure Policy Assignment (Allowed virtual machine size SKUs)
# Allow VM creation only for the following SKUs
$SKUs=”Standard_A1_v2″,
“Standard_A2_v2”,
“Standard_A2m_v2”,
“Standard_A4_v2”,
“Standard_A8_v2”,
“Standard_B1ms”,
“Standard_B1s”,
“Standard_B2ms”,
“Standard_B2s”,
“Standard_B4ms”,
“Standard_D1_v2”,
“Standard_D16ds_v5”,
“Standard_D16s_v3″
$PolicyAssignmentName=”Allowed virtual machine size SKUs”
$Policy = Get-AzPolicyDefinition -Builtin | Where-Object {$_.Properties.DisplayName -eq “Allowed virtual machine size SKUs”}
$Parameter = @{“listOfAllowedSKUs”=@($SKUs)}
New-AzPolicyAssignment -Name $PolicyAssignmentName -PolicyDefinition $Policy -Scope “/subscriptions/$SubscriptionId” -PolicyParameterObject $Parameter -Location $location -AssignIdentity
We can use the following commands to check is assignment has been assigned
$Policy = Get-AzPolicyAssignment -Name “Allowed virtual machine size SKUs”
#($Policy).Properties.Parameters
($Policy).Properties.Parameters.listOfAllowedSKUs | fl
NOT ALLOWED RESOURCE TYPES
Setup Policy Assignment using Portal
To set up this policy assignment, type Not Allowed Resource Types in search and navigate to the Assign buttons as presented in the following pictures.
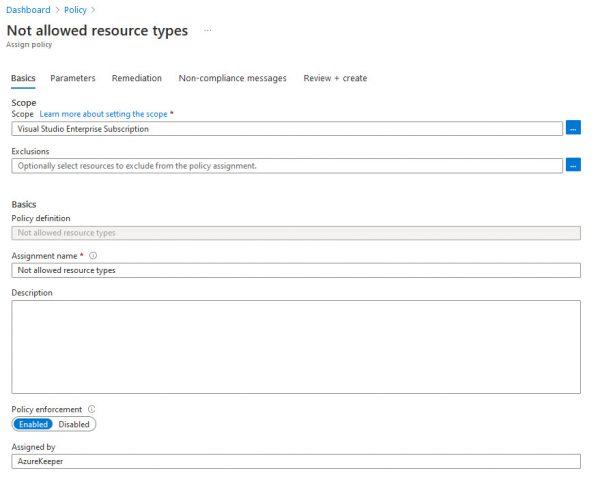
On the Basic tab leave it as default. By default, this policy will be assigned to the whole subscription
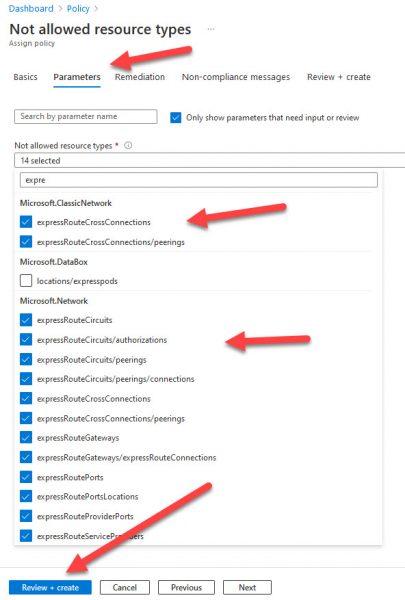
Navigate to the Parameters tab and select all services which you do not want to be available for your users
Setup Policy Assignment using PowerShell
You can use this script to create policy assignment. Just add your resources s in $BlockResources variable.
$Subscriptionid=”XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX”
$location=”Canada Central”
# Create an Azure Policy Assignment (Not allowed resource types)
# Dendy creation only for the following resource types
$BlockResources=
“microsoft.network/expressroutecircuits”,
“microsoft.network/expressroutegateways”,
“microsoft.network/p2svpngateways”,
“microsoft.network/vpngateways”
$PolicyAssignmentName=”Not allowed resource types”
$Policy = Get-AzPolicyDefinition -Builtin | Where-Object {$_.Properties.DisplayName -eq “Not allowed resource types”}
$Parameter = @{“listOfResourceTypesNotAllowed”=@($BlockResources)}
New-AzPolicyAssignment -Name $PolicyAssignmentName -PolicyDefinition $Policy -Scope “/subscriptions/$SubscriptionId” -PolicyParameterObject $Parameter -Location $location -AssignIdentity -Verbose
We can use the following commands to check is assignment has been assigned
$Policy = Get-AzPolicyAssignment -Name “Not allowed resource types”
#($Policy).Properties.Parameters
($Policy).Properties.Parameters.listOfResourceTypesNotAllowed | fl