Overview of the process
When you have a large Azure installation, you want to limit which address ranges your end users can create.
We can accomplish this with Azure Policy. However, there are no build-in policies, so we will need to create custom policies.
In our example, we want to limit Vnet Address space creation to all Address spaces starting with 10.4.X.X and using only /24 subnet mask.
We will need to create two Azure Policies and assign them to Subscription.
Policies to be created.
- Azure Policy denies VNet address space creation if it is not starting with 10.4 space.
- Azure Policy which denies creation of any other subnet mask then /24
Azure Policy denies VNet address space creation if it is not starting with 10.4 space.
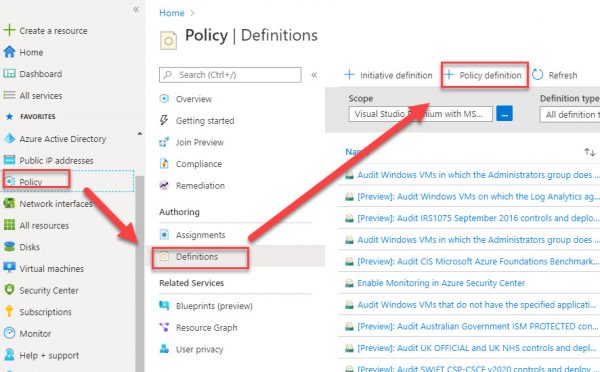
To create “Azure Policy which denies VNet address space creation if it is not starting with 10.4” navigate to :
Policies-Definitions and select + Policy Definition
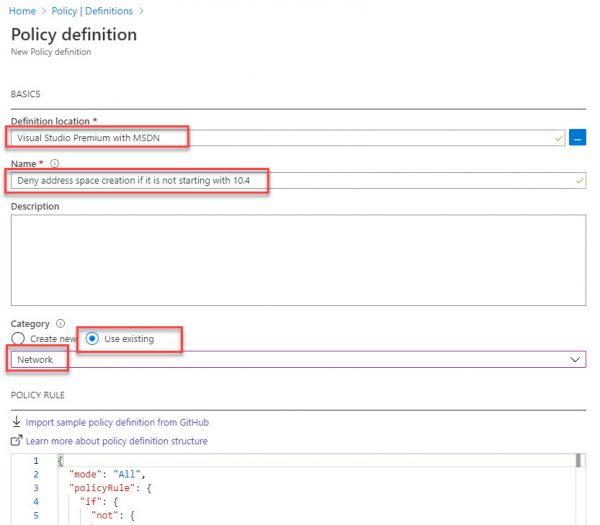
On the Policy Definition blade navigate to your subscription and type the name for your policy.
For the category, you can use existing network category
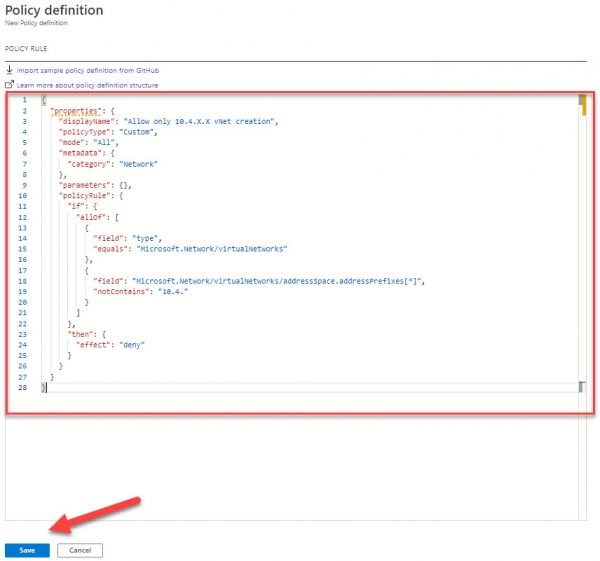
Navigate to the Policy rule, delete existing entries form windows and paste entires form the following file:
Azure Policy which denies VNet address space creation if it is not starting with 10.4 space.
Hit the Save button to save the policy.
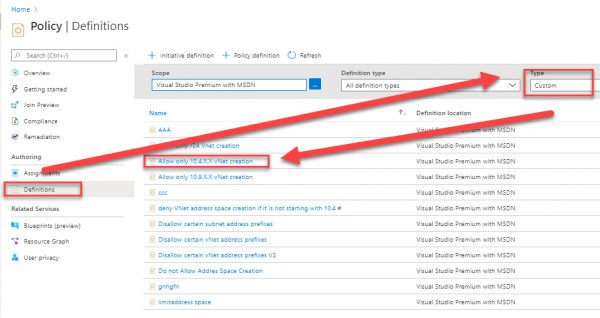
Go back to Policy-Definitions and change type to custom in filtering windows.
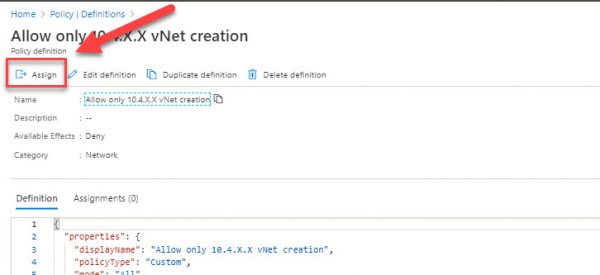
Double click to your policy and the new blade will open.
On a new blade, click Assign.
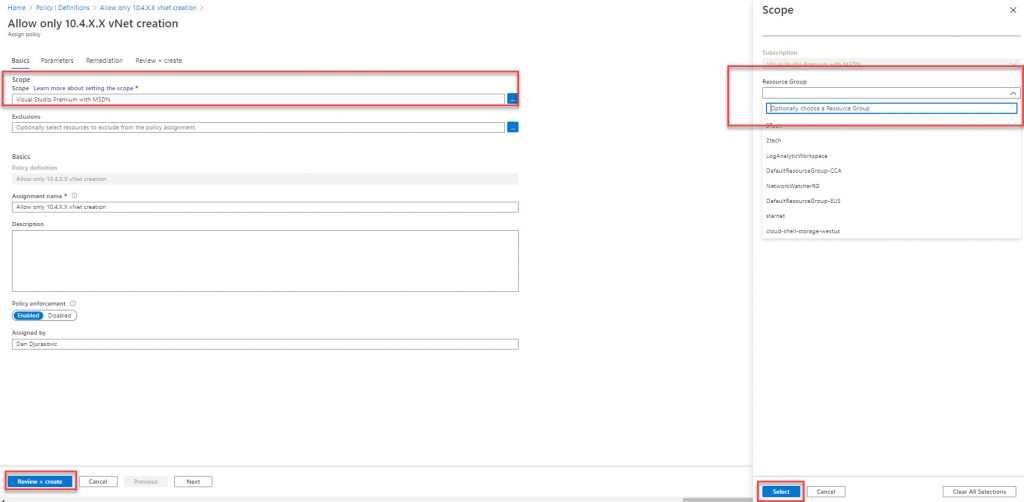
On the Right side, a new blade will show you scope. You can choose subscription or resource groups.
Press Save and press Review + Create to assign a policy.
Let test how the policy works.
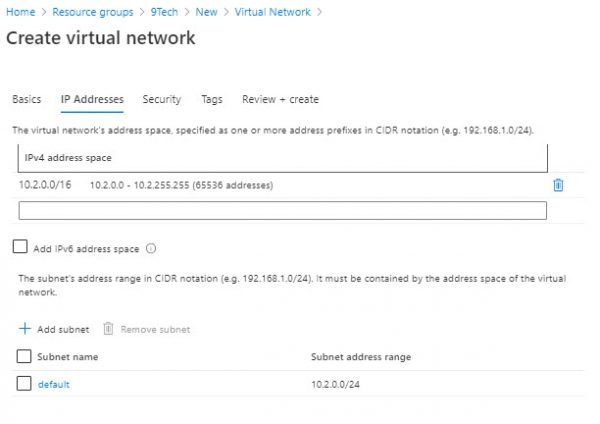
Try to create a new VNet using default options. As you can see in our example we are trying to create address space 10.2.0.0/16.
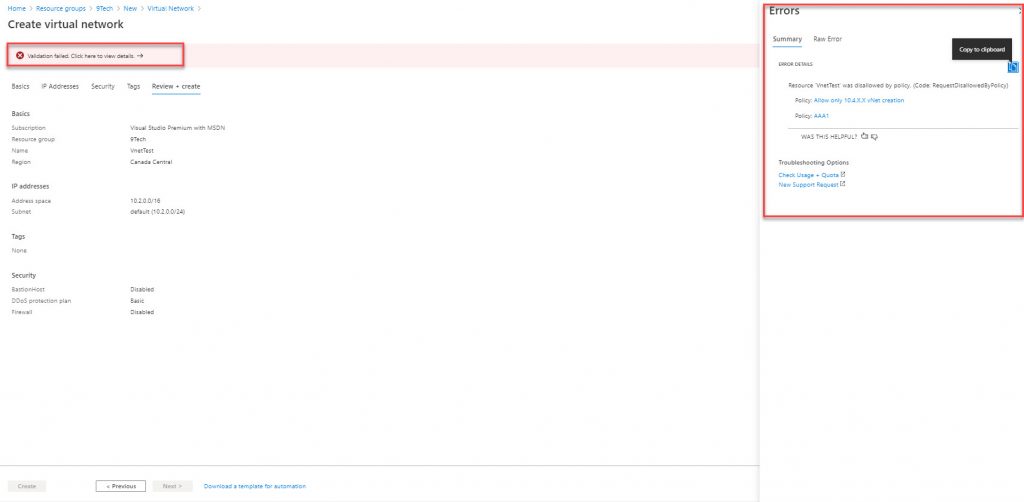
Validation is going to fail and Errors will show you that vNet can not be created because the address space you specified does not match address space specified in our Policy.
Azure Policy which denies creation of any other subnet mask then /24
To create a policy which allows only /24 subnet mask creation, repeat the following process and use the following file
Azure Policy which denies creation of any other subnet mask then 24
Customize Policy
If you want to customize policies, we recommend changing settings in RED.
Azure Policy which denies VNet address space creation if it is not starting with 10.4 space.
{
“properties”: {
“displayName”: “Allow only 10.4.X.X vNet creation“,
“policyType”: “Custom”,
“mode”: “All”,
“metadata”: {
“category”: “Network”
},
“parameters”: {},
“policyRule”: {
“if”: {
“allOf”: [
{
“field”: “type”,
“equals”: “Microsoft.Network/virtualNetworks”
},
{
“field”: “Microsoft.Network/virtualNetworks/addressSpace.addressPrefixes[*]”,
“notContains”: “10.4.”
}
]
},
“then”: {
“effect”: “deny”
}
}
}
}
Azure Policy which denies creation of any other subnet mask then /24
{
“properties”: {
“displayName”: “Allow only /24 VNet creation“,
“policyType”: “Custom”,
“mode”: “All”,
“metadata”: {
“category”: “Network”
},
“parameters”: {},
“policyRule”: {
“if”: {
“allOf”: [
{
“field”: “type”,
“equals”: “Microsoft.Network/virtualNetworks”
},
{
“field”: “Microsoft.Network/virtualNetworks/addressSpace.addressPrefixes[*]”,
“notContains”: “/24”
}
]
},
“then”: {
“effect”: “deny”
}
}
}
}
11.10.4.0/24 is valid but unwated
How do i allow list of CIDRs?
How I do prevent creation of any virtual network, exception of only the network administrator users that manage the private network within Azure Portal